Tough Times for Hackers – Part 2: Applying the EN 18031 standard
Cybersecurity is shifting into the focus of European regulation. According to the EU Radio Equipment Directive, by August 2025, products with radio technology and internet access must protect networks and personal data and prevent fraud. The EN18031 standard is designed to assist manufacturers in implementation. Part 2 looks into its application.
Author: Gerhard Stelzer
The EU Cyber Resilience Act (CRA) introduces completely new cybersecurity requirements for electronic devices. It was published in the Official Journal of the EU in November 2024 and is therefore applicable law. However, no standards exist for it yet. A transitional period is therefore expected to apply until December 2027, after which new products will have to comply with the CRA.
Until then, the Radio Equipment Directive (RED) is intended to enhance cybersecurity, at least for all wireless devices. To this end, the EU amended the RED in 2022, supplementing Article 3(3), to now define the following three sub-points:
- 3(3)(d) to ensure network protection
- 3(3)(e) to safeguard personal data and privacy
- 3(3)(f) to ensure protection against fraud
The deadline for implementation now runs until August 1, 2025. After that, no wireless devices may be placed on the EU market unless they meet the cybersecurity requirements of the RED.
EN 18031 standard facilitates implementation
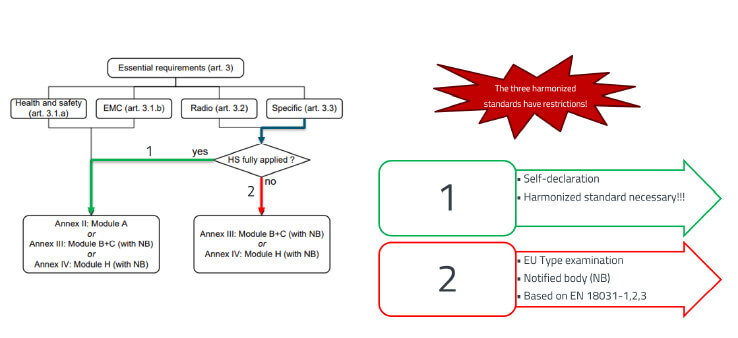
The EN 18031 standard translates the cybersecurity aspects of the RED into specific testing procedures and was developed by the CENELEC standards organization on behalf of the EU. In October 2024, CENELEC submitted EN 18031 to the European Commission for review. The standard was harmonized in January 2025, meaning that new products no longer have to be certified by an accredited testing service provider (Figure 5). A self-declaration of conformity is sufficient.
Conformity test, taking the example of a WiFi module
The conformity test is illustrated here taking the example of Würth Elektronik’s IoT WiFi module Cordelia-I [5]. The WiFi module is fully compliant with the RED, including the cybersecurity extension 2022/30/EU from January 2022. The Cordelia-I module complies with IEEE 802.11 b/g/n, operates in the 2.4 GHz band, and is characterized by the following features:
- Zero-touch provisioning with QuarkLink (more on this later)
- Secure UART-to-cloud bridge (transparent mode)
- Small form factor: 19 x 27.5 x 4 mm3
- Sleep mode <10 μA
- Intelligent antenna configuration (2-in-1 module)
- Output power +18 dBm peak (1DSSS)
- Receiver sensitivity: –92 dBm (1 DSSS, 8% PER)
- Industrial temperature range: -40°C up to +85°C
- authentication and authorization
- data protection
- software and firmware security
- network security
- physical security
- incident response and management
- user awareness and education
- compliance with regulations and documentation
According to the RED, cybersecurity for wireless devices such as radio modules must be ensured in accordance with Article 3(3). For the Cordelia-I radio module, only Article 3(3)(d) – protection of the network is relevant, as neither personal data under 3(3)(e) nor financial data under 3(3)(f) is processed. It follows that Cordelia-I must be tested in accordance with EN 18031-1:2024.
The core requirements of EN 18031-1:2024 for a wireless device in terms of cybersecurity are:
The standard provides assistance for testing using decision trees. A cascading question structure is used, with “yes” and “no” answers provided. If the answer is “yes”, meaning the result is “not applicable”, the respective test is not required for the product under test. For the final question in the cascade, the “yes” answer means a “pass” for the test. A “no” answer results in a “fail,” and corrective action may be required.
The cybersecurity space is volatile and constantly evolving, for example, with the CRA coming into effect at the end of 2027. It is important to conduct a cybersecurity risk analysis at an early stage of the design process and to continuous this analysis throughout the product lifecycle. The implementation of cybersecurity involves more than just hardware and software. “Policies” also play an important role, such as a vulnerability reporting system, software updates, ease of installation and maintenance, etc. The goal must be “security by design”.
Design of a security concept for an embedded device
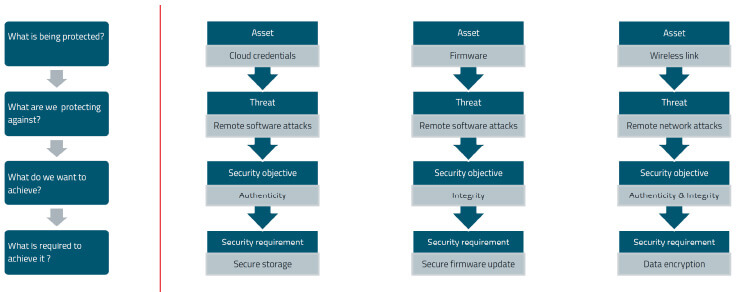
When designing a security concept for an embedded device, several key questions have to be asked and answered: Which asset needs protection? What does the threat look like? Which security objective do we have? What do we need to achieve it? Figure 6 illustrates these security requirements for different assets.
The current state of cybersecurity measures in a typical IoT application encompasses a range of security elements:
- A secure “root of trust“ is a unique identity along with a cryptographic key associated with it. As the entire security chain relies on this foundation of trust, it is essential that a RoT is unique, unchangeable, and unclonable.
- Secure boot is a security feature that ensures that only trusted software is loaded during a device’s boot process. It is a firmware-based process that verifies the digital signature of the bootloader and all subsequent operating system components before they are loaded into memory. The goal of secure booting is to prevent the execution of malware and other malicious software and compromising the system during the boot process.
- Firmware over-the-air (FOTA) is a method by which the firmware of an electronic device is updated wirelessly, usually over a secure connection. FOTA updates can be used to fix bugs, add new features, or patch security gaps in the device’s firmware.
- Every interface to the outside world must be considered vulnerable and secured accordingly. A range of standard protocols can be used for authentication and encryption of communication interfaces.
- Secure storage areas are isolated execution environments that provide hardware-based security for sensitive data and code. They are designed to protect against attacks that attempt to access or modify data in memory or steal cryptographic keys.
These general measures to ensure cybersecurity have been implemented in the Cordelia-I WiFi module (Figure 7). The WiFi radio module includes the following security features:
- 10-byte non-manipulable unique device ID
- Secure boot
- Secure storage with encrypted file system for storing certificates and other credentials
- Secure firmware over-the-air update
- Secure socket – Transport Layer Security protocol TLSv1.2
- Secure WiFi connection according to WPA3
- Hardware-accelerated crypto engine
Secure cloud connection
To ensure a secure connection to the cloud, the device and the cloud should perform mutual authentication, followed by exchanging a session key, which is then used to encrypt the communication channel. This is usually done using the TLS protocol.
To establish a mutual TLS connection, the following cryptographic elements must be present on the device and in the cloud. The assets must also be properly aligned with each other.
On the device side, these are:
- Device ID: Unique device identity that is unchangeable and tamper-proof.
- Device key: This is a private key that is unique to each device and must be kept secret.
- Device certificate: This certificate contains the public key associated with the device private key.
- Root CA: This is the root CA (Certificate Authority) of the cloud, which is used to authenticate the cloud endpoint.
The process of storing these parameters on the end device is known as “device provisioning”.
On the cloud side this entails:
- List of the device IDs: A whitelist of device IDs that are authorized to establish connections.
- Device certificates: Public keys corresponding to the device IDs to enable device authentication.
The process of storing these parameters on the cloud endpoint is known as “cloud onboarding”. These cryptographic values must be stored securely on both the device and the cloud endpoint. Disclosure of these values at any stage of the device manufacturing lifecycle can compromise security. Human interaction with these cryptographic assets often poses the greatest threat. Therefore, the following steps must be followed to ensure maximum security.
The Cordelia-I module with the QuarkLink platform enables a secure cloud connection through zero touch device provisioning and secure cloud onboarding. In addition, full device management – including remote cloud migration – can be carried out throughout the lifecycle of a device.
Zero-touch provisioning with QuarkLink
In this process, the device is configured with all the parameters required to connect to the cloud platform, including cryptographic resources, without any need for human intervention.
This involves configuring multiple parameters, including the cryptographic assets on the device as described above. The Cordelia-I module, together with the QuarkLink platform, enables zero-touch provisioning. Each module is delivered with a unique, pre-installed, and hardware-based tamper-proof key set.
The private key is securely linked to the hardware and cannot be read out by the application. The application software can only access the public key and use the private key for further cryptographic operations.
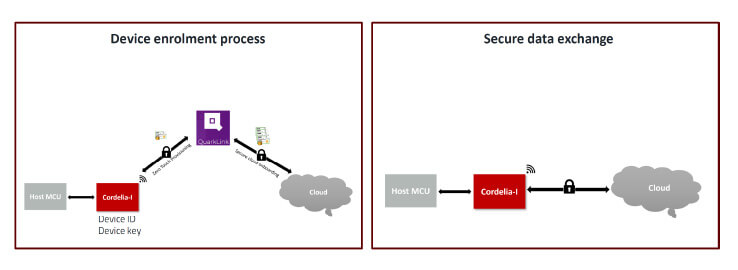
Secure cloud onboarding
In this process, the cloud endpoint is configured to enable an authenticated connection with the end devices. The parameters “list of device IDs” and “device certificates”, as mentioned previously, are stored at the cloud endpoint for this purpose.
The QuarkLink platform enables secure device onboarding with most major cloud service providers, including self-hosted servers. This is achieved with authenticated REST APIs provided by the cloud service providers.
Würth Elektronik’s partnership with Crypto Quantique
The combination of Crypto Quantique’s QuarkLink security software platform with Würth Elektronik’s wireless modules enables automatic and secure connection of thousands of sensor nodes to local or cloud-based servers. The platform enables device provisioning, onboarding, security monitoring, as well as renewing and revoking certificates and keys – all carried out with just a few clicks on a graphical user interface. Users thus have access to all the features required for managing IoT devices over their lifecycle.
Jan Norder and Pascal Baranger from Würth Elektronik will take the stage at Evertiq Expo Kraków 2025, May 28, and give a presentation entitled ‘Securing the future: navigating cybersecurity regulations in IoT’. Are you interested in cyber security? This year's edition of the Polish fair will be particularly focused on cyber security and security in general. Registration for the event is already open!


