Tough times for hackers – Part 1: Basic regulatory principles
Cybersecurity is shifting into the focus of European regulation. According to the EU Radio Equipment Directive, by August 2025, products with radio technology and internet access must protect networks and personal data and prevent fraud. The EN18031 standard is designed to assist manufacturers in implementation.
Author: Gerhard Stelzer
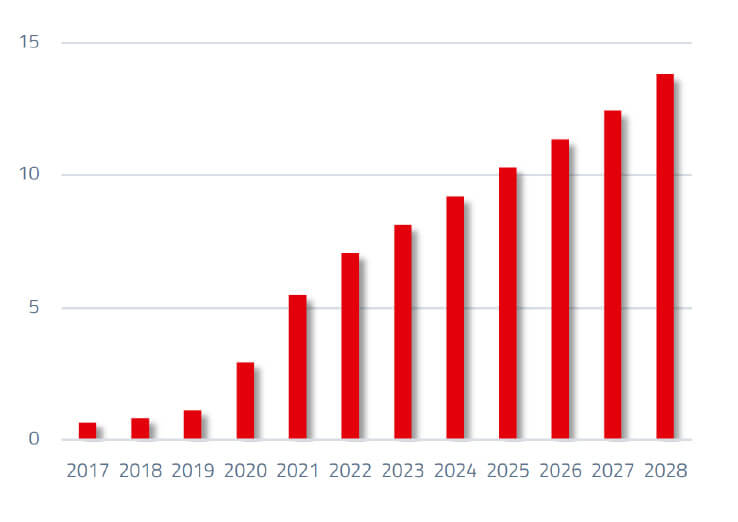
According to the European Commission, a ransomware attack occurs somewhere in the world every 11 seconds. These ransomware attacks alone are estimated to have caused costs of 20 billion euros worldwide in 2021. According to Statista (the German independent market research institute), the annual global volume of damage from cybercrime is estimated to reach around 10 trillion dollars in 2025 (Figure 1). At the same time, it is estimated that cybercriminals will have launched around 10 million DDoS (Distributed Denial of Service) attacks by then.
The European Commission wants to make Europe more resilient and secure against cyberattacks and has adopted the “Cyber Resilience Act” (CRA) to achieve this. The CRA is the first EU-wide legislation of its kind to establish common cybersecurity rules for manufacturers and developers of products with “digital elements” (hardware and software).
The Cyber Resilience Act is intended to ensure that
- wired and wireless products on the EU market which are connected to the internet, as well as software, become more secure.
- manufacturers remain responsible for the cybersecurity of their products throughout their entire lifecycle.
- consumers are properly informed about the cybersecurity of the products they purchase and use.
Cybersecurity risks
Cyberattacks can spread across the borders of the EU single market within minutes. So, the CRA addresses two issues:
- The low level of cybersecurity in many of these products and – even more importantly – the fact that many manufacturers do not provide updates to eliminate security vulnerabilities. While manufacturers of products with digital elements may sometimes suffer reputational damage if their products are not secure, the costs of security vulnerabilities are mainly borne by professional users and consumers. This limits the incentives for manufacturers to invest in secure design and development and to provide security updates.
- Companies and consumers often lack sufficient and accurate information when it comes to selecting secure products. They often don’t know how to ensure that the products they have purchased are configured securely.
The new regulations address these two aspects by focusing on the issue of updates and by providing up-to-date information for customers.
Principles of the Cyber Resilience Act
The Cyber Resilience Act stipulates that products with digital elements may only be placed on the market if they meet certain basic cybersecurity requirements. It requires manufacturers to consider cybersecurity in the design and development of products with digital elements.
In terms of the information and instructions for the end user, the Cyber Resilience Act requires manufacturers to provide transparency regarding the cybersecurity aspects that must be communicated to customers.
A key aspect of the proposal is that the entire product lifecycle is covered, specifically the obligation for manufacturers and developers to define a support period covering the expected lifetime of the product and to provide security updates during this period.
These obligations apply to economic operators, ranging from manufacturers to distributors and importers, with regard to placing products with digital elements on the market.
Based on the new legal framework for product legislation in the EU, manufacturers will undergo a conformity assessment procedure to demonstrate compliance with the established requirements for a product.
This could be done through self-assessment or a third-party conformity assessment, depending on the risk associated with the product in question.
Once the product's compliance with the applicable requirements has been verified, the manufacturer and developer issue an EU declaration of conformity and may affix the CE mark. The CE mark indicates that products with digital elements comply with the Cyber Resilience Act, allowing them to be freely distributed within the single market.
The Cyber Resilience Act was published in the Official Journal of the EU in November 2024 and is expected to become mandatory from December 2027. Until then, the EU Radio Equipment Directive (RED) is to be extended to include cybersecurity aspects to improve cybersecurity, at least in radio equipment. More below.
Advantages of the Cyber Resilience Act
The Cyber Resilience Act will significantly benefit the various stakeholders. Companies will soon only need to comply with one package of cybersecurity regulations across the EU.
The legislation will reduce the number of cybersecurity incidents and the costs of handling incidents as well as the reputational damage to companies. This would strengthen consumer and business customer trust in companies and products, thereby increasing the demand for products with digital elements both within and outside the EU.
At the same time, when selecting a product with digital elements, the consumers and users will benefit from more information and clearer instructions on how to use it. As a result of lower security risks and incidents, consumers and citizens will benefit from better protection of fundamental rights, such as data protection and privacy.
The Cyber Resilience Act also has the potential to become an international benchmark beyond the EU single market. The EU legislative standards will facilitate its implementation and be an advantage for EU manufacturers in global markets.
Non-compliant products
The member states must appoint market surveillance authorities responsible for enforcing the obligations under the Cyber Resilience Act.
In the event of non-compliance, market surveillance authorities may require operators to rectify non-compliance and eliminate the risk. They may prohibit or restrict the availability of a product on the market or order that the product be withdrawn or recalled. Each of these authorities will be able to impose fines on companies that fail to comply with the regulations. The CRA sets maximum limits for fines that are provided for in national laws in the event of non-compliance.
Interaction with other rules
The Cyber Resilience Act aims to harmonize the EU regulatory landscape by introducing cybersecurity requirements for products with digital elements and by avoiding overlapping requirements arising from different legal regulations. This creates greater legal certainty for operators and users across the EU, as well as better harmonization of the European single market, thus improving the conditions for operators wishing to enter the EU market.
The Cyber Resilience Act will serve as a valuable complement to the NIS2 Directive (Network and Information Systems Directive 2), recently adopted by the European Parliament and the Council. The NIS2 Directive introduces cybersecurity requirements – including security measures in the supply chain and reporting obligations for essential and important entities – to strengthen the resilience of the services they provide.
A higher level of cybersecurity for products with digital elements would make it easier for the entities covered by the NIS2 Directive to comply with the regulations and would enhance the security of the entire supply chain.
The Cyber Resilience Act also applies to radio equipment that falls within the scope of the Delegated Regulation under the Radio Equipment Directive 2014/53/EU. The CRA is aligned with the requirements of the Delegated Regulation of the RED, including the specific standards required.
Radio Equipment Directive 2014/53/EU (RED)
Smart devices and toys, smart cameras, and a range of other connected radio devices, such as cell phones, laptops, dongles, alarm systems, and home automation systems, are examples of devices that carry the risk of being hacked and privacy compromised when connected to the internet. In addition, wearable radio devices (e.g., rings, bracelets, pocket clips, headsets, fitness trackers, etc.) can monitor and record a range of sensitive user data over an extended period (such as location, temperature, blood pressure, heart rate). This data may be transmitted not only via the internet but also through insecure short-range communication technologies. The Radio Equipment Directive 2014/53/EU (RED) establishes a legal framework for placing radio equipment on the single market (Figure 2). It concerns binding market access conditions for radio equipment [2], and a product's compliance with the RED is required for the CE marking. The RED applies to electrical and electronic devices that can use the frequency spectrum for communication and/or radio purposes. Member States (MS) take corrective actions for non-compliant radio equipment through their national market surveillance authorities.

Article 3 of the RED sets out the essential requirements that radio equipment placed on the EU market must meet. Article 3(1)(a) sets out the essential requirements regarding health and safety, Article 3(1)(b) the essential requirements concerning electromagnetic compatibility, and Article 3(2) the essential requirements regarding the effective and efficient use of the radio spectrum. Moreover, Article 3(3) sets out additional essential requirements that apply to those categories or classes of radio equipment specified in the relevant Delegated Acts of the Commission.
New cybersecurity rules in force from August 2025
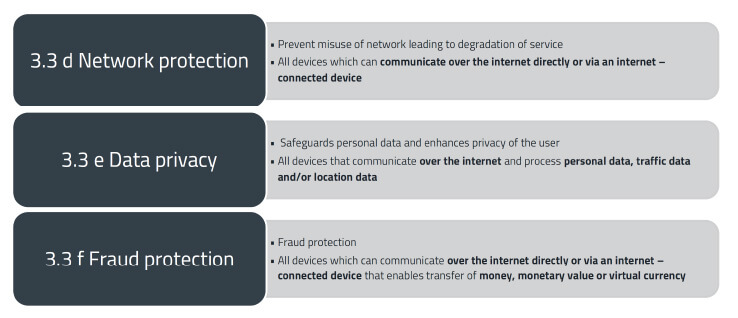
Article 3(3) of the RED now defines the new cybersecurity requirements for radio devices. This concerns the following three points from the second subparagraph of Article 3(3) (Figure 3):
- 3(3)(d) to ensure network protection
- 3(3)(e) to safeguard personal data and privacy
- 3(3)(f) to ensure protection against fraud
The new EN18031 series of standards for cybersecurity in radio equipment aids with implementing the cybersecurity requirements of the Radio Equipment Directive (RED).
EN18031 – Cybersecurity in radio equipment
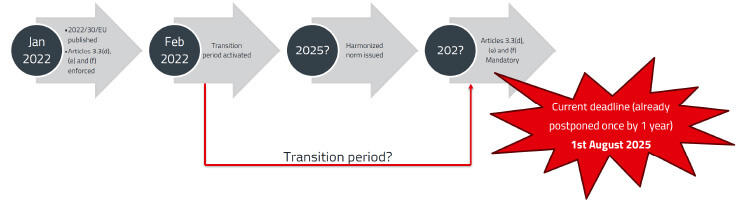
The introduction of new requirements through Delegated Regulation 2022/30 of the Radio Equipment Directive 2014/53/EU presents significant challenges for the industry. The new EN 18031 series – consisting of EN 18031-1, EN 18031-2, and EN 18031-3 – is intended to help manufacturers demonstrate the compliance of their products with the stricter requirements. From August 1, 2025, the affected devices must meet these requirements (Figure 4).
EN 18031 specifies the requirements of the Radio Equipment Directive concerning cybersecurity and comprises three parts:
- EN 18031-1 covers radio equipment with internet connectivity. Part 1 of this standard sets out testing procedures and conditions to assess the compliance of internet-enabled radio equipment with Article 3(3)(d) of the RED. It requires that radio equipment must not have any harmful effects on networks or their operation.
- EN 18031-2 deals with radio equipment that processes data. According to Part 2 of the standard, data-processing radio equipment is tested regarding Article 3(3)(e) of the RED for the protection of personal data.
- EN 18031-3 deals with radio equipment that processes virtual money or monetary value. It defines the testing procedures for Article 3(3)(f) of the RED, which test the functions for fraud protection.
The EN18031 series of standards was submitted to the EU Commission for review and harmonization by CENELEC (European Committee for Electrotechnical Standardization), in October 2024.
Principles of EN 18031
The EN 18031 standard provides a comprehensive and flexible framework for the security of radio equipment. It considers the complexity and diversity of modern devices and provides manufacturers with clear guidelines for implementing robust security measures. The Cyber Regulation portal provides a concise overview. The EN18031 standard was developed by CENELEC on behalf of the EU and submitted to the EU Commission for review in October 2024. If the harmonization of the standard has not been completed, products must still be certified by accredited testing service providers.
According to the Cyber Regulation, the relevant principles are:
- Security by Design: Security aspects must be considered as early as the development process.
- Structured threat analysis: EN 18031 recommends the use of the STRIDE model. This model helps manufacturers think systematically about potential threats by considering six main categories of threats: Spoofing, Tampering, Repudiation, Information disclosure, Denial of service and Elevation of privilege.
- Categorization of security measures: The standard divides security requirements into five main categories:
– Identifying: Recognizing security risks
– Protecting: Preventing or limiting security incidents
– Detecting: Tracing security incidents
– Reacting: Acting appropriately to identified incidents
– Recovering: Restoration after a security incident - Assets: The standard introduces the term “assets” to define the main objectives of security measures. These include network assets, security assets, data protection assets, and financial assets. This approach helps manufacturers develop targeted protection measures for the most important parts of their product.
- Mechanisms: The standard uses “mechanisms” to address specific security requirements. This approach allows the requirements to be applied flexibly to different types of devices and deployment scenarios.
- Practical evaluation methods: The standard provides specific tools for assessing compliance:
– Decision trees help determine whether specific requirements are applicable
– Specifications for technical documentation indicate the information that manufacturers must provide
– Guidelines for security tests indicate how implementation of the requirements can be verified
EN 18031 is generally intended to provide a balanced and practical approach to improve the security of radio equipment. The standard recognizes that there is no one-size-fits-all solution for all devices and instead provides a framework within which manufacturers can develop the appropriate security measures for their specific products.
Gerhard Stelzer studied electrical engineering and information technology at the Technical University of Munich, where he graduated with an engineering degree. He then went on to work in the development of high-speed optical communication technology at Siemens AG and switched to technical journalism in 1995, working for the publication “Elektronik”. Since 2021, he has been Senior Technical Editor at Würth Elektronik eiSos.
Jan Norder and Pascal Baranger from Würth Elektronik will take the stage at Evertiq Expo Kraków 2025, May 28, and give a presentation entitled ‘Securing the future: navigating cybersecurity regulations in IoT’. Are you interested in cyber security? This year's edition of the Polish fair will be particularly focused on cyber security and security in general. Registration for the event is already open!


